Correlated Network Policies
Kubernetes architecture requires the network layer to enable any-to-any Pod communication. That makes lots of SREs very unhappy. Operators don’t like critical workloads such as databases to be accessible by any pod in the cluster. For that purpose NetworkPolicies were introduced to Kubernetes.
NetworkPolicies restrict ingress or egress traffic to the Pods using Pod label selectors. Imaging figuring out what NetworkPolicies apply to the application? It is very hard.
For that purpose, Kubevious comes with a correlated network policies view. Kubevious detects which NetworkPolicies apply to an application and combine all those network policies into a single network view.
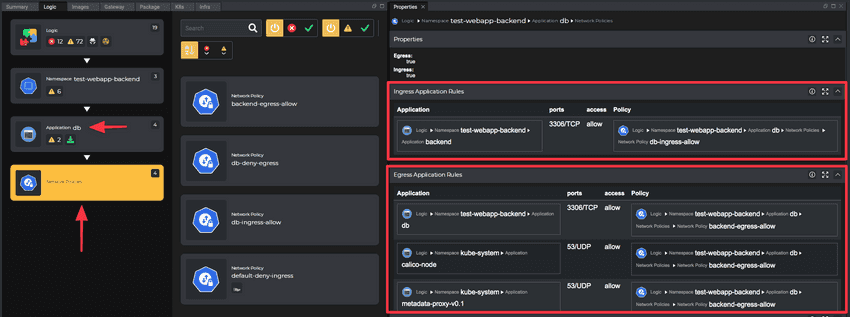
Ingress and Egress Rules properties present target applications for which the traffic is allowed and the policy that grants that permission. Those are active links, so clicking on the application or the policy would navigate further analysis and troubleshooting.
Custom Network Policy Validation Rules
Just like anything else visible in Kubevious GUI, Network Policies can be used in writing custom validation rules to detect conditions that are relevant and important for your own organization.
For example, a custom rule below prevents exposing MySQL databases to namespaces other than example. The Target Script selects Applications that are using mysql image.
Target Script:
Logic()
.child('Namespace')
.child('Application')
.child('Container')
.child('Image')
.filter(({item}) => {
if (item.props.name == "mysql") {
return true;
}
return false;
})
.ancestor('Application')
The Rule Script checks if any Network Policies are defined on the applications. It then checks which apps are allowed to communicate with the MySQL database on port 3306 and which namespace do those apps belong to.
Rule Script:
if (item.hasChildren('Network Policies'))
{
var netpolicies = item.children('Network Policies')[0];
var egressRules = item.getProperties('egress-app');
if (egressRules && egressRules.rows) {
for(const rule of egressRules.rows)
{
if (rule.ports == "3306/TCP")
{
if (!rule.dn.startsWith("root/logic/ns-[example]"))
{
error('We do not allow using MySQL from namespaces other than EXAMPLE.');
}
}
}
}
}
else
{
error('No network policies defined on MySQL.');
}
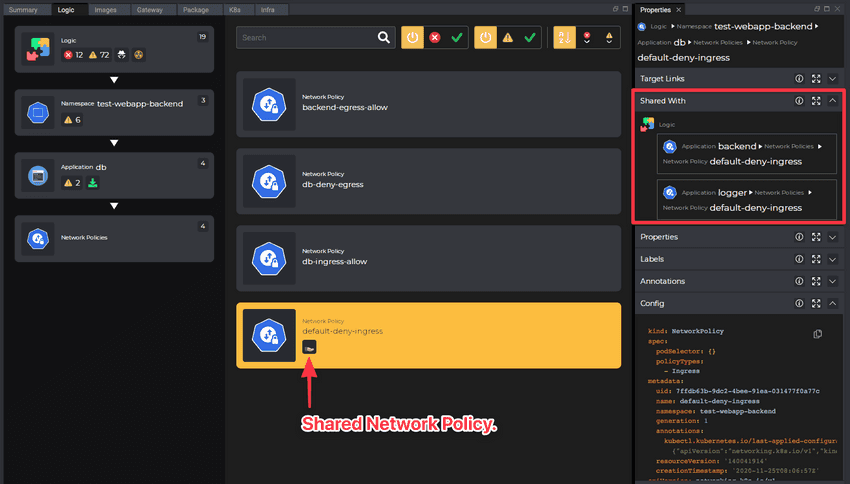
Shared Configuration
Just like in the case of ConfigMaps, the Network Policies can be marked with “Shared-By” flag. That would mean that the NetworkPolicy is used to control network traffic to other applications. Any changes to this NetworkPolicy would affect other applications as well. Learn more regarding identifying blast radius.