Correlated RBAC
Things get messy when it comes to Kubernetes RBAC. There are too many indirections and links to navigate to identify permissions granted to Pods, Users, and Groups. Kubevious provides a correlated view across Roles, Bindings, ServiceAccounts, Applications, Users, and Groups.
Application Permissions
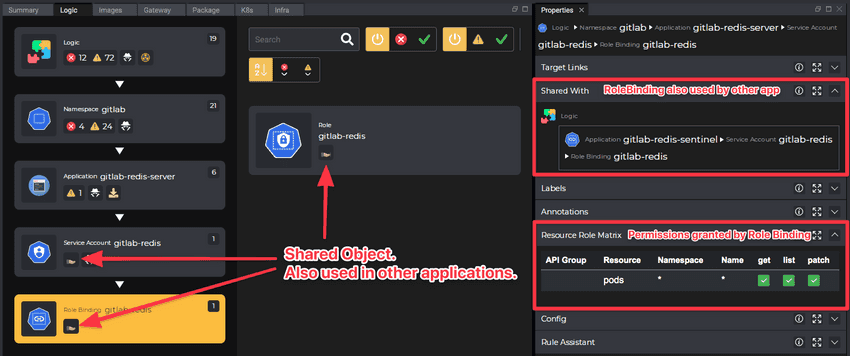
Kubevious determines how ServiceAccounts, Bindings, and Roles are related to Applications and correlates them under the Service Account node in the Application Logic view. In such applications, the ServiceAccount node would include the list of attached Bindings as children.
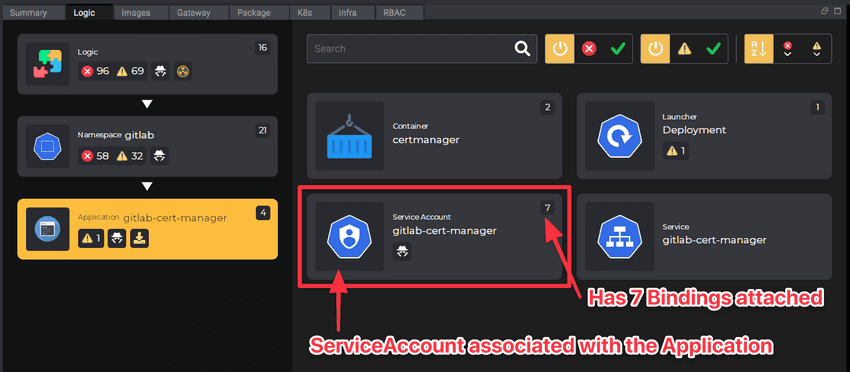
Kubevious goes one step further and combines permissions across all relevant roles and presents them in a single role matrix.
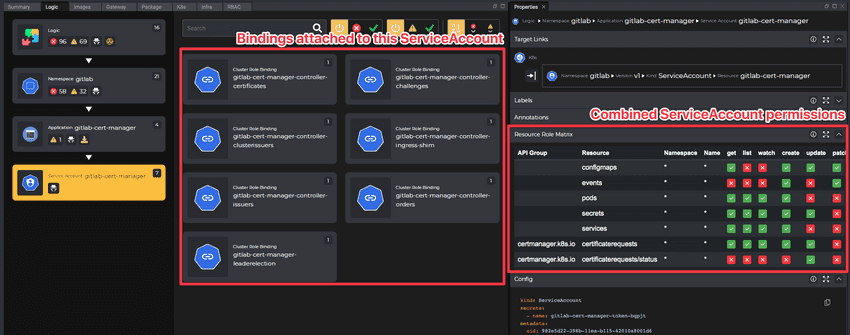
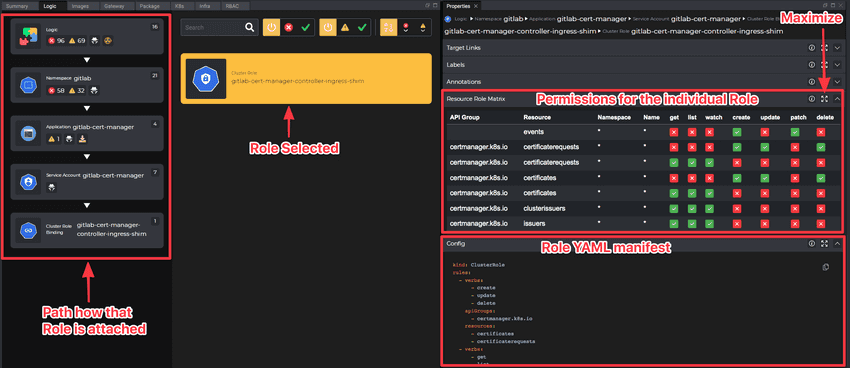
Following the same navigation method, it is possible to drill down the Bindings and individual roles for more detailed analysis or access the Role YAML manifest. Both on the Binding and Role levels, the Role Matrix is available for quick access.
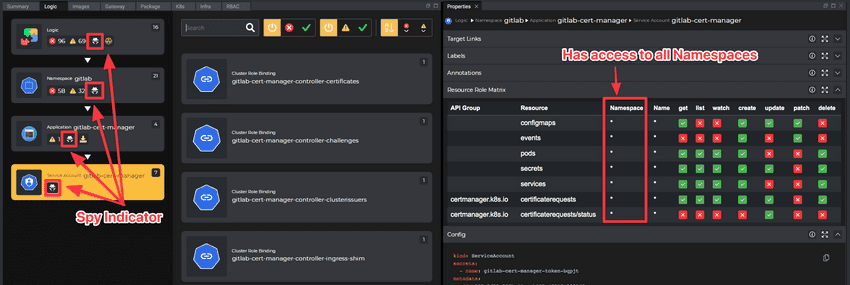
Spy Workloads
Kubevious detects Applications that access Kubernetes API resources beyond the Namespace scope. Such configurations are marked with a Spy icon. The Spy icon is propagated up the tree. So, by looking at the Namespace, there is a clear indication of some infrastructure workloads or if ServiceAccount permissions are not configured correctly.
Shared Configuration
Just like in case of ConfigMaps, the ServiceAccounts, Roles and Bindings can be marked with “Shared-By” flag. That would mean that the ServiceAccount, Role or Binding is used elsewhere, and any changes to would affect other applications as well. Learn more regarding identifying blast radius.
User and Group Permissions
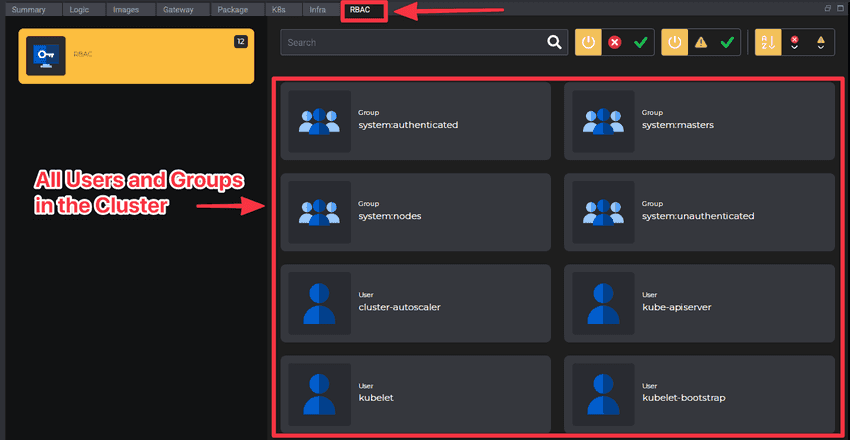
Let’s run a thought experiment. You’ve created the certificate for the user using OpenSSL, created kube-config file, granted permissions to a user(or a group) using Roles and Bindings. You did this about 100 times. Fast forward three weeks. How long would it take to answer a simple question: “How many users and groups do we have, and what permissions do they have? “. Using traditional tools that would mean going over every single Binding and Role. That’s why we created a dedicated RBAC view in Kubevious.
Kubevious RBAC view identifies which Users and Groups are used in the cluster.
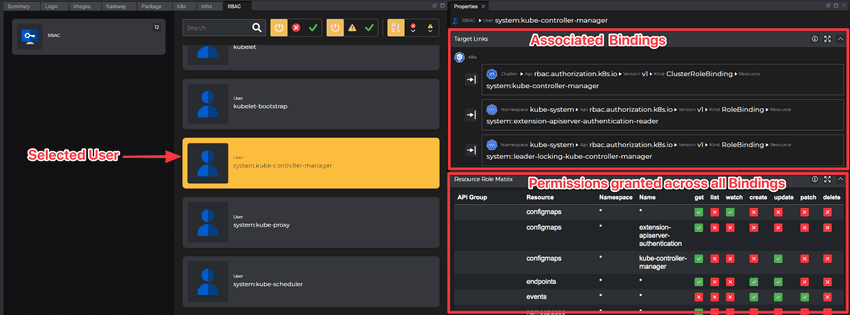
Selecting a User exposes all Bindings used to grant Roles to the User, and just like in the case of ServiceAccounts - presents the correlated role matrix view for the selected User. The same applies to any Group.
Kubevious RBAC Videos
Kubevious RBAC role matrix walkthrough:
Writing a custom rule to detect Applications that are accessing Kubernetes Secrets:
NOTE. We have upgraded the UI, so the look, feel and some navigation is different in the videos at the time of the recording.